See every service your team uses. Authorised or not - get full visibility.
Uniqkey’s Service Overview gives you a real-time map of your organisation’s digital footprint. From sanctioned tools to shadow IT, get visibility into every service linked to work accounts—so you can reduce risk, recover spend, and take control of your IT environment.
.avif)


















Know what’s being used and what shouldn’t be. Stay one step ahead with complete oversight.
30% of SaaS licenses purchased by companies go unused, representing significant resource wastage.
IT oversight simplified for management teams.
Many organizations fail to track license usage effectively, leading to redundant or forgotten subscriptions.
Shadow IT Detection
Bring hidden tools into the light.
Monitor services connected to work emails to expose unofficial apps. Take back control and enforce policies that keep your organisation secure, compliant, and efficient.
.avif)
.webp)

Informed Resource Allocation
Spend less. Use more.
Use real usage data to reduce redundant licences and refocus budgets where it counts. Clean up your IT stack and eliminate waste across teams and departments.
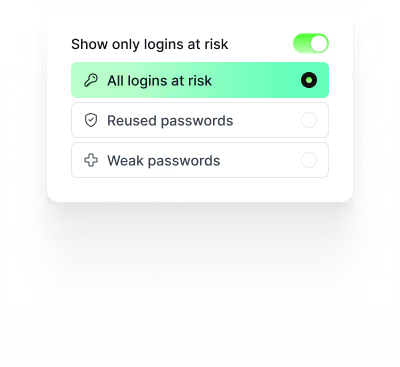
Security at a Service Level
Evaluate service-specific risks.
Uniqkey assigns security scores to each service based on your team’s password strength. See where vulnerabilities exist and prioritise action where it matters most.
.webp)

Trusted by leading European organisations.
Loved by customers, hated by hackers.
.svg)




.svg)


_HighPerformer_HighPerformer.svg)



“Uniqkey isn’t just a vendor; they’re a partner genuinely committed to understanding our needs and helping us achieve secure, streamlined operations."

Features that bring you from chaos to compliance.
Loved by customers, hated by hackers.
Leading the next era of
European access security.






.webp)

.webp)
.webp)